Automating 1Password CLI with --session
In a our previous post, we looked at generating a 1password session without requiring user input. Today we will look at generating a one-time (30-minute) token on your local machine and only sharing that with your build servers.
If you do not have 1password CLI setup, then please read our previous post on getting started, but as soon as it talks about generating sessions using expect then head back over here.
Generation 1Password token using --raw
As we saw previously, we can op you can generate a session token. Below we have two small changes.
op signin --raw my aforward@hey.com > opsession-
We added the
--rawflag so that we only output the 1password token -
We redirect the output to a
opsessionfile.
Now instead of building a forever re-useable opsession (as we did with expect), we now have a 30-minute opsession token (within a file) that we can share with our build server as seen below (step B).
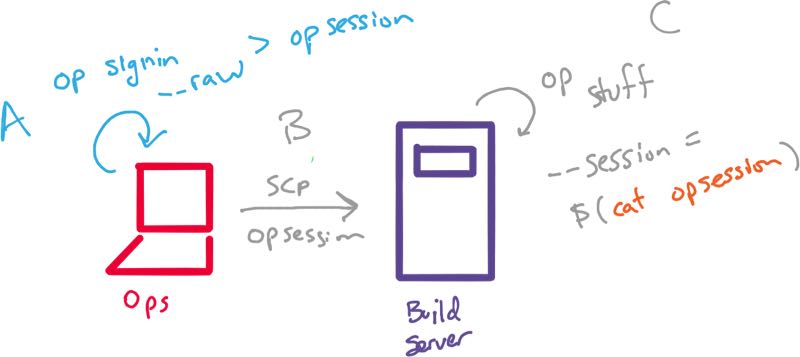
Our automation scripts can now use the --session flag pointing to the contents
of our token with cat opsession. For example.
op get item db_password --session $(cat opsession)In this approach, we are still generating 1password sessions locally, and then sharing the token on our build servers. Those environments now have 30-minutes access to the secrets it needs (DB passwords, API secrets, etc) in a completely autonomous way.
Happy automation!